Home » Force-directed algorithms
Category Archives: Force-directed algorithms
Dataset of Visualization of Dynamic Graphs
We provided three distribution functions (e.g., Gaussian distribution, Poisson distribution and random distribution) to simulate the time intervals for updating (insertion of new nodes and edges) the graphs.
Moreover, we selected three datasets with varying size, temporal edges and duration of time interval in the dataset.
- Dataset email-Eu-core-temporalDept3 (*) is an incoming and outgoing traffic for E-Mail graph. A separate edge is created for each recipient of the e-mail.
- Dataset CollegeMsg (**) is a temporal graph comprised of private messages sent on an online social network at the University of California.
- Dataset soc-sign-bitcoinalpha (***) is a transaction graph in BitCoin Alpha.
- (*) Paranjape, Ashwin, Austin R. Benson, and Jure Leskovec. “Motifs in temporal networks.” Proceedings of the Tenth ACM International Conference on Web Search and Data Mining. 2017.
- (**) Panzarasa, Pietro, Tore Opsahl, and Kathleen M. Carley. “Patterns and dynamics of users’ behavior and interaction: Network analysis of an online community.” Journal of the American Society for Information Science and Technology 60.5 (2009): 911-932.
- (***) Kumar, Srijan, et al. “Edge weight prediction in weighted signed networks.” 2016 IEEE 16th International Conference on Data Mining (ICDM). IEEE, 2016.
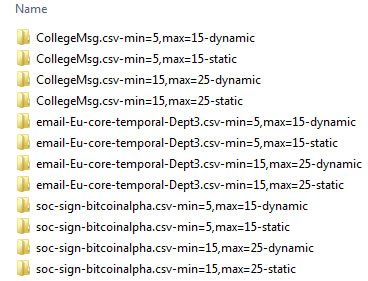
Each distribution contains static (the name of folder ends with static) and dynamic datasets (the name of folder ends with dynamic):
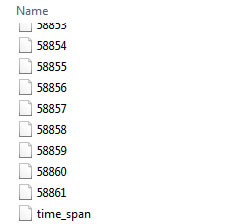
Each dataset contains a time_span file (the time intervals for updating the graphs) and graph files. The data structure of graph file is the same as the Dataset of CNCAH Network.
Download:
- Gaussian Distribution (22.17 GB after extraction, 554,288 files)
- Poisson Distribution (11.08 GB after extraction, 277,144 files)
- Random Uniform Distribution (11.00 GB after extraction, 277,144 files)
If you use the dataset for your research/development, please cite the following paper:
Cheong, Se-Hang, Yain-Whar Si, and Raymond K. Wong. "Online force-directed algorithms for visualization of dynamic graphs." Information Sciences 556 (2021): 223-255.
Force-directed algorithms for schematic drawings and placement: A survey
Force-directed algorithms have been developed over the last 50 years and used in many application fields, including information visualisation, biological network visualisation, sensor networks, routing algorithms, scheduling, graph drawing, etc. Our survey provides a comprehensive summary of developments and a full roadmap for state-of-the-art force-directed algorithms in schematic drawings and placement.
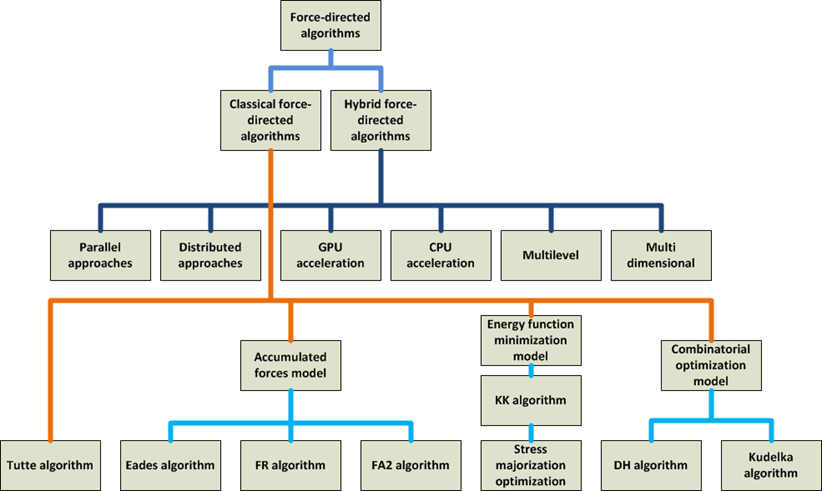
We classified the model of force-directed algorithms into classical and hybrid. The classical force-directed algorithms are further classified as follows: (a) accumulated force models, (b) energy function minimisation models, and (c) combinatorial optimisation models. The hybrid force-directed algorithms are classified as follows: (a) parallel and hardware accelerated models, (b) multilevel force-directed models, and (c) multidimensional scaling force-directed algorithms. Five categories of application domains in which force-directed algorithms have been adopted for schematic drawings and placement are also summarised: (a) aesthetic drawings for general networks, (b) component placement and scheduling in high-level synthesis of very-large scale integration (VLSI) circuits design, (c) information visualisation, (d) biological network visualisation, and (e) node placement and localisation for sensor networks.
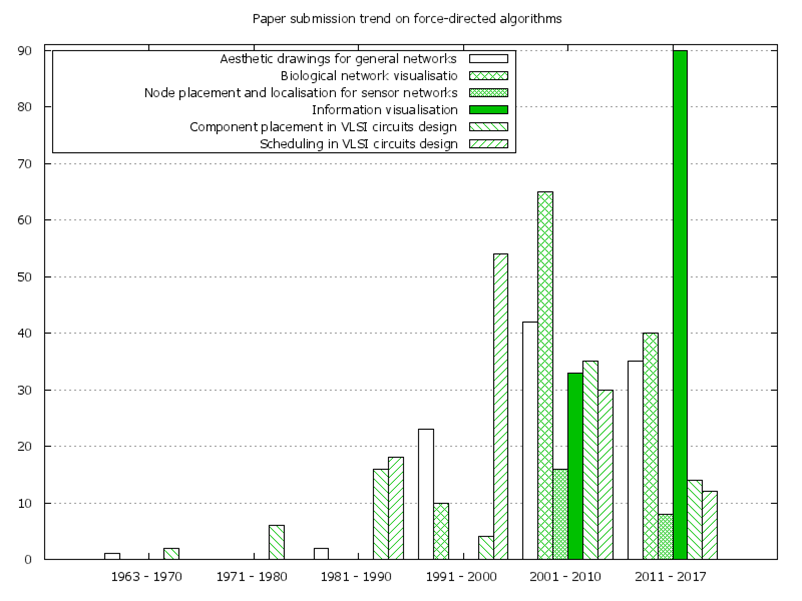
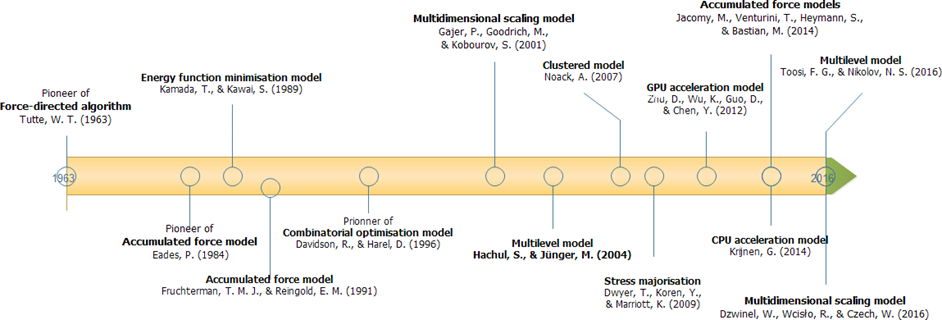
The author’s version of a work that was accepted for publication can be downloaded from http://eric.lostcity-studio.com/wp-content/uploads/2019/08/Force-directed-algorithms-for-schematic-drawings-and-placement:a-Survey.pdf. Se-Hang Cheong, Yain-Whar Si. "Force-directed algorithms for schematic drawings and placement: A survey", Information Visualization, Accepted and to appear, Sage, 2019.
Snapshot Visualization of Complex Graphs with Force-directed Algorithms
Force-directed algorithms are widely used for visualizing graphs. However, these algorithms are computationally expensive in producing good quality layouts for complex graphs. The layout quality is largely influenced by execution time and methods’ input parameters especially for large complex graphs. The snapshots of visualization generated from these algorithms are useful in presenting the current view or a past state of an information on timeslices. Therefore, researchers often need to make a trade-off between the quality of visualization and the selection of appropriate force-directed algorithms.
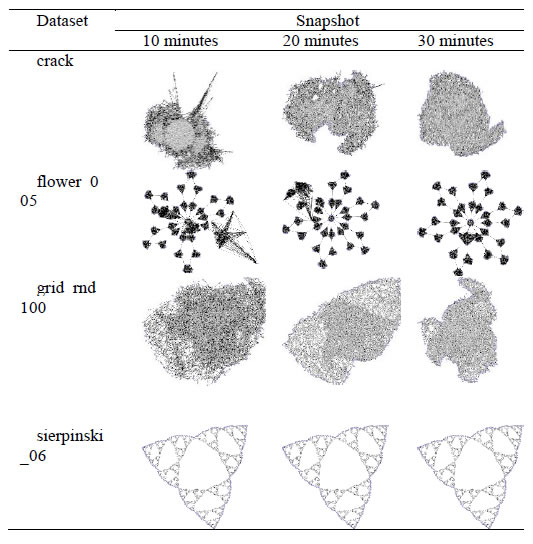
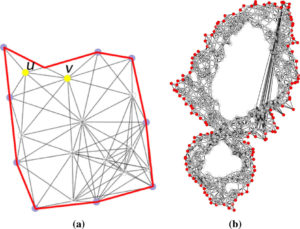
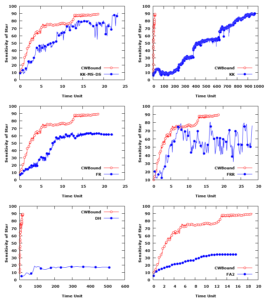
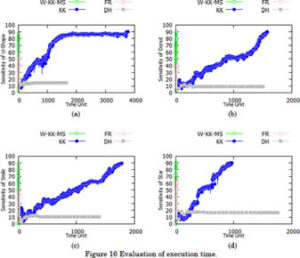
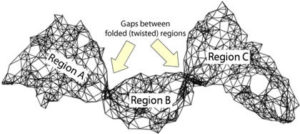
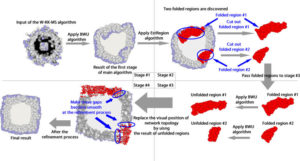
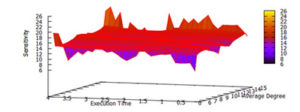
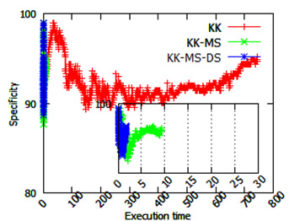
In this paper, we evaluate the quality of snapshots generated from 7 force-directed algorithms in terms of number of edge crossing and the standard deviations of edge length. Our experimental results showed that KK, FA2 and DH algorithms cannot produce satisfactory visualizations for large graphs within the time limit. KK-MS-DS algorithm can process large and planar graphs but it does not perform well for graphs with low average degrees. KK-MS algorithm produces better visualizations for sparse and non-clustered graphs than KK-MS-DS algorithm.
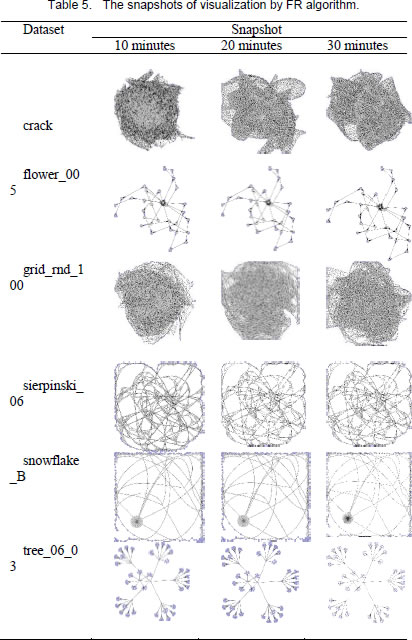
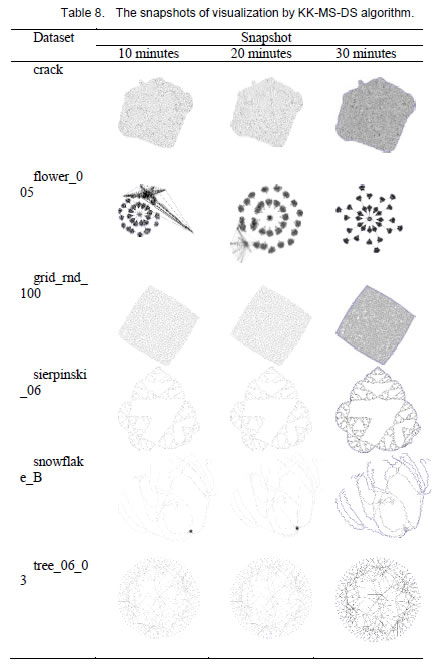
The author’s version of a work that was accepted for publication can be downloaded from http://eric.lostcity-studio.com/wp-content/uploads/2019/08/Snapshot-Visualization-of-Complex-Graphs-with-Force-directed-Algorithms.pdf.
Se-Hang Cheong, Yain-Whar Si. "Snapshot Visualization of Complex Graphs with Force-directed Algorithms", Proceedings of the IEEE International Conference on Big Knowledge (ICBK), pp. 139-145, IEEE Press, 2018.