There are real cases where mobile phones have been contributed for successful rescues in recent catastrophic disasters. Examples of such cases have been reported in history.
- http://mashable.com/2010/01/20/haiti-iphone-survivor/#mKSyzKKquiqy
- http://lubbockonline.com/filed-online/2011-10-24/5-earthquake-survivors-saved-rubble-turkey
- http://www.asiaone.com/News/Latest%2BNews/Asia/Story/A1Story20110224-265107.html
However, Public Switched Telephone Networks (PSTN), including cellular networks could be disrupted during natural disasters, such as earthquakes, hurricane, tsunami, etc.
In such situations, mobile phone users may not be able make emergency calls since cellular signal is likely to be unavailable due to the destruction of land-based network infrastructures. Although we cannot assume that all people trapped under debris will have access to their mobile phones, it is possible that some of them may still have access to their mobile phones when they are trapped under the debris or when they are waiting to be rescued.
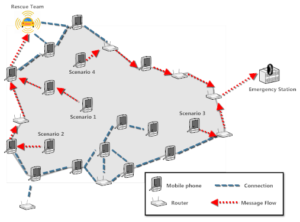
This paper proposes a system for automatically forming ad hoc networks using mobile phones and battery-powered wireless routers for emergency situations. The system also provides functions to send emergency messages and identify the location of victims based on the network topology information.
The author’s version of a work that was accepted for publication can be downloaded from http://eric.lostcity-studio.com/wp-content/uploads/2019/08/Saving-Lives:Design-and-Implementation-of-Lifeline-Emergency-Ad-Hoc-Network.pdf.
Se-Hang Cheong, Yain-Whar Si, Leong-Hou U. “Saving Lives: Design and Implementation of Lifeline Emergency Ad Hoc Network”, International Journal of Pervasive Computing and Communications, Accepted and to appear.